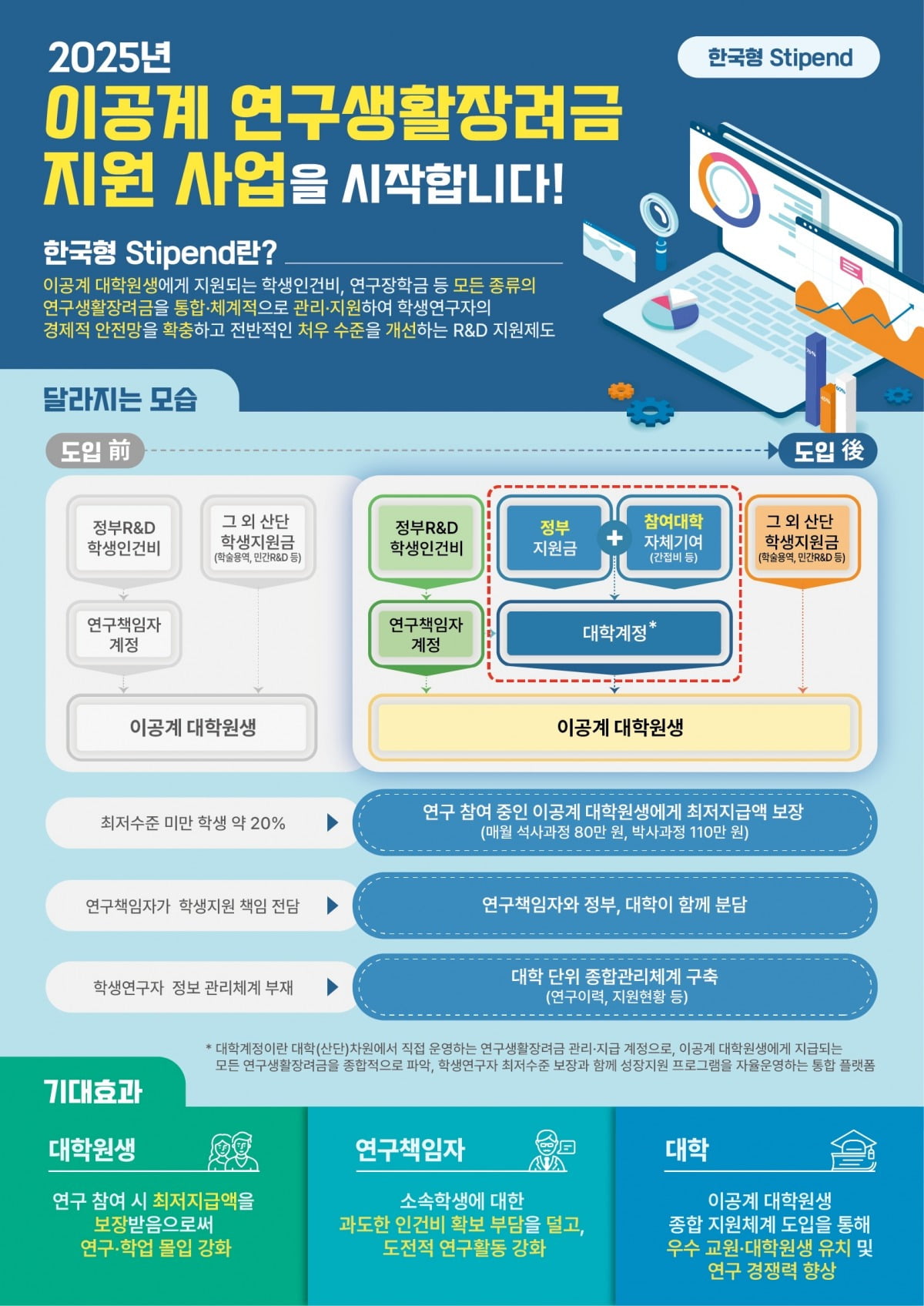
Introduction
Secure and efficient access to SAP applications is crucial for maintaining operational excellence and high productivity for users. As organizations embrace hybrid work models and mobile workforce solutions, traditional VPN (Virtual Private Network) based approaches to SAP system access are increasingly showing their limitations.
At the same time, organizations are looking beyond traditional access methods, demanding solutions that combine straightforward system accessibility with rapid deployment and streamlined setup requirements.
This blog post explores how AWS Verified Access is transforming SAP user access security by implementing zero-trust principles to more granular access policies that can improve security posture of SAP systems especially those that needs to provide mobile workforce solutions.
The Challenges of Traditional VPN Solutions for SAP
Traditional VPN solutions present several significant challenges:
- Performance Bottlenecks: VPNs often create network congestion during peak usage, leading to degraded performance for critical SAP operations. This delays mission critical business processes which will impact company bottom lines.
- Limited Scalability: Traditional VPN infrastructure struggles to accommodate growing user bases and increased remote work demands. This can be seen during the previous COVID pandemic when users are mandated to work from home, and they could not execute business processes in SAP because the VPN Gateway was full.
- Complex Management:> Managing VPN configurations, certificates, and client software across diverse user devices creates substantial administrative overhead, especially in the company data centre.
- Broad Network Access: VPNs typically grant extensive network access, conflicting with zero-trust security principles and modern compliance requirements which mandates a principle of least privileges.
- Inconsistent User Experience: VPN connections can be unreliable and slow, particularly affecting SAP GUI and Fiori applications that require stable and reliable connectivity to the organization’s SAP Landscape.
- High implementation effort: Setting up VPN devices is time consuming and costly. Roll out and management of clients on end users notebooks require significant effort for the central IT team
Introducing a New Paradigm in security to access SAP Applications
AWS Verified Access represents a paradigm shift in user access to SAP applications . This modern approach eliminates the need for traditional VPNs while providing Identity-based access control, continuous trust verification, granular policy enforcement, simplified administration and enhanced user experience.
Key Features and Benefits of AWS Verified Access for SAP
With AWS Verified Access application owners can apply zero trust access controls to their SAP applications by constantly verifying each access request against granular, conditional access policies.
- Identity-Centric Security. Verified access integrates with existing identity providers (IdP), such as Microsoft Azure AD (Entra), Okta, Ping, and others. It provides real-time user authentication and authorization that support for SAML 2.0 and AWS IAM Identity Center.
- Contextual Access Control. Verified Access is able to implement device security posture assessment, location-based access policies, role-based access management and dynamic policy evaluation.
- Enhanced Performance. Verified Access provides a direct and optimized connection paths to SAP systems, thus reducing network latency, improve performance and provide more consistent user experience to SAP systems.
- Simplified Administration. Verified Access provides centralized policy management through AWS Cedar Policy Language and authorization engine. It provides automated compliance reporting, real-time access monitoring and reduced infrastructure maintenance.
In summary, AWS Verified Access enables you to implement least-privilege access principles, continuous device security monitoring, configure granular access policies, establish clear security baselines and maintain comprehensive audit logs. With the support of non-HTTP(S) protocols such as TCP, SSH, and RDP, you can use AWS Verified Access not only for SAP Fiori (HTTP(S)) but also for SAP GUI access.
How do we implement AWS Verified Access for SAP
When implementing Verified Access for SAP workload on AWS, you can configure it by following Tutorial: Get started with Verified Access in the same AWS Account of your SAP system. This will jumpstart your implementation and guide you all the technical considerations that must be taken into account. Below is the architecture on how AWS Verified Access can be used with SAP on AWS.
Figure 1. Architecture of AWS Verified access for SAP on AWS
When implementing Verified access for RISE with SAP on AWS, you can configure it by following Tutorial: Get started with Verified Access in a separate AWS Account that is managed by your team. The AWS Verified Access VPC will need to be integrated to RISE VPC through Transit Gateways, so the network traffic is routed correctly to the target system. Below is the high-level architecture on how AWS Verified Access can be used with RISE with SAP.
Figure 2. Architecture of AWS Verified access for RISE with SAP on AWS
High-Level Implementation Phases of AWS Verified Access for SAP
- Assessment Phase Evaluate existing SAP landscape, identify user access patterns such as whether the remote users will need SAP GUI or SAP Fiori, then you define security policy based on these user’s access patterns and data or system classification. Consider AWS Partners solutions when you need to implement specialized capabilities, such as continuous assessment on users device, locations, network connectivity with JAMF or CrowdStrike to implement Zero Trust Access principle.
- Planning Phase You can design access policies based on your organization security framework. You can integrate identity provider (IdP) such as Microsoft Azure AD or Entra, IAM Identity Center, Okta or others as the first baseline. On top of this, you can also implement a more granular device trust checks, such as enforcing certain patch levels, or an up-to-date virus scanner, or other requirements.
- Deployment Phase Consider a phased approach to your Verified Access deployment strategy. Validate your configuration choices, ensure appropriate scaling of the solution, and verify the support mechanisms needed.
- Optimization Phase With its real-time observability and logging, you will be able to understand the analytics and gain insights on the usage over time. With this data, you can refine the access policies to your SAP system, and leverage on feedback from users to further optimize your configuration.
- Measure your success in SAP Some improvement metrics that you can measure, include: reduction in connection issues, faster order processing times for mobile sales workers in SAP, faster maintenance order closure for maintenance workers in SAP, decrease in access-related support tickets, and improved remote user satisfaction.
Steps to configure AWS Verified Access to your SAP systems using IAM Identity Center as a trust provider.
Prerequisites:
- AWS IAM Identity Center enabled in the AWS Region that you prefer. For more information, see Enable AWS IAM Identity Center in the AWS IAM Identity Center User Guide.
- A security group to allow network access to SAP applications.
- A public TLS certificate in AWS Certificate Manager when configuring AWS Verified Access for HTTP(s) based access (i.e. SAP Fiori). Use an RSA certificate with a key length of 1,024 or 2,048.
- A public hosted domain and the permissions required to update DNS records for the domain. (example: Amazon Route 53)
- An IAM policy with the permissions required to create an AWS Verified Access instance. For more information, see Policy for creating Verified Access instances.
- Set the system environment variable SAP_IPV6_ACTIVE=1 as per SAP note 1346768 (requires a SAP S-user ID to access), this is needed when accessing SAP application using Verified Access endpoint from SAP GUI.
Implementation Steps:
- Create a Verified Access Trust Provider: After IAM Identity Center is enabled on your AWS account, you can use the following procedure to set up IAM Identity Center as your trust provider for Verified Access.
- Create a Verified Access instance: You use a Verified Access instance to organize your trust providers and Verified Access groups. Use the following procedure to create a Verified Access instance, and then attach a trust provider to Verified Access or detach a trust provider from Verified Access..
- Create a Verified Access group: You use Verified Access groups to organize endpoints by their security requirements. When you create a Verified Access endpoint, you associate the endpoint with a group. Use the following procedure to create a Verified Access group.
- Create a load balancer endpoint for Verified Access: Verified Access endpoint represents an application. Each endpoint is associated with a Verified Access group and inherits the access policy for the group. Use the following procedure to create a load balancer endpoint for Verified Access for SAP application.
- Configure DNS for the Verified Access endpoint: For this step, you map your SAP application’s domain name (for example, www.myapp.example.com) to the domain name of your Verified Access endpoint. To complete the DNS mapping, create a Canonical Name Record (CNAME) with your DNS provider. After you create the CNAME record, all requests from users to your application will be sent to Verified Access.
- Add a Verified Access group-level access policy: FAWS Verified Access policies allow you to define rules for accessing your SAP applications hosted in AWS. When you create a Verified Access group or create a Verified Access endpoint, you have the option to define the Verified Access policy. You can create a group or endpoint without defining the Verified Access policy, but all access requests will be blocked until you define a policy. Alternatively, you can add or change a policy on an existing Verified Access group or endpoint after it has been created. Refer to the following sample statements to derive one for your application as per your requirements.
- Test the connectivity to your application: You can now test connectivity to your application by entering your SAP application’s domain name into your web browser, for HTTP(S) based access such as SAP Fiori.
For connecting on non-HTTP(S) protocol (using SAP GUI), you must install Connectivity Client by following the below steps.
- Download the Connectivity Client: Download the client using the following procedure.
- Export client configuration file : Use the following procedure to export the configuration information required by the client from your Verified Access instance.
- Connect to the application: Use the following procedure to connect to an application using the connectivity client. It takes 2-3 minutes for Connectivity Client to establish the route to the Verified Access endpoint. To ensure the route is established you can type the command netstat -r and check if you see active route on /57 like highlighted below.
Figure 3. Example netstat result for route created by Connectivity Client.
AWS Verified Access Pricing
In HTTP(s) application, such as SAP Fiori or SAP Portal, AWS Verified Access is priced based on application hours and GB of data processed. In Non-HTTP(s) application, such as SAP GUI, AWS Verified Access is based on the non-HTTP endpoint hours and number of connections. You can find out more details here.
Conclusion
AWS Verified Access represents the future of user access security to SAP systems, offering a more secure, efficient, and user-friendly alternative to traditional VPNs. By embracing this modern approach, organizations can enhance their security posture while improving user experience and reducing administrative overhead.
The integration capabilities with existing identity providers, combined with granular access controls and simplified management, make AWS Verified Access an ideal solution for organizations looking to modernize their SAP access security strategy.
Read more on AWS for SAP blogs to get inspiration on how you can get more out of your SAP investment. Get started with AWS Verified Access today !
Join the SAP on AWS Discussion
In addition to your customer account team and AWS Support channels, we have recently launched re:Post – A Reimagined Q&A Experience for the AWS Community. Our AWS for SAP Solution Architecture team regularly monitor the AWS for SAP topic for discussion and questions that could be answered to assist our customers and partners. If your question is not support-related, consider joining the discussion over at re:Post and adding to the community knowledge base.
Credits
I would like to thank the following team members for their contributions: Arne Knoeller, Derek Ewell, Adam Hill and Spencer Martenson.












 English (US) ·
English (US) ·